Network Access Control (NAC) in Cybersecurity

Many threats to an organization's cybersecurity exploit vulnerabilities in the organization network to gain initial access to systems and information. To help mitigate these risks, organizations should focus on building secure networks.
Examples of the controls that an organization may use to contribute to building a secure network include network access control (NAC) solutions; network perimeter security controls, such as firewalls; network segmentation, and the use of deception as a defensive measure.
One of the basic security objects set forth by most organizations is controlling access to the organization's network.
Network access control (NAC) solutions help security professionals achieve two cybersecurity objectives: limiting network access to only authorized individuals and ensuring that systems accessing the organization's network meet basic security requirements.
The 802.1X protocol is a common standard used for NAC. When a new device wishes to gain access to a network, either by connecting to a wireless access point or plugging into a wired network port, the network challenges that device to authenticate using the 802.1X protocol. A special piece of software, known as a supplicant, resides on the device requesting to join the network. The supplicant communicates with a service known as the authenticator that runs on either the wireless access point or the network switch. The authenticator does not have the information necessary to validate the user itself, so it passes access requeests along to an authentication server using the Remote Authentication Dial-In User Service (RADIUS) protocol. If the user correctly authenticates and is authorized to access the network, the switch or access point then joins the user to the network. If the user does not successfully complete this process, the device is denied access to the network or may be assigned to a special quarantine network for remediation.
The diagram below shows all the devices involved in 802.1X
authentication for network access control.
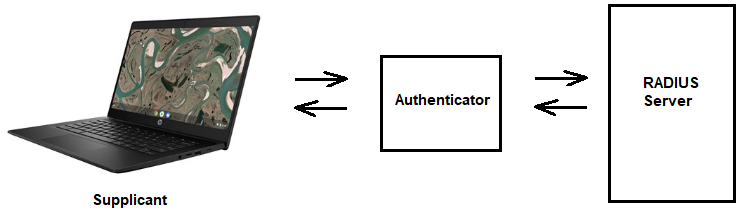
In an 802.1X system, the device attempting to join the network runs an NAC supplicant, which communicates with an authenticator on the network switch or wireless access point. The authenticator uses RADIUS to communicate with an authentication server.
Many NAC solutions are available on the market, and they differ in two major ways:
Agent-based vs Agentless- Agent-based solutions, such as 802.1X, require that the device requesting access to the network run special software designed to communicate with the NAC service. Agentless approaches to NAC conduct authentication in the web browser and do not require special software.
In-Band vs Out-of-Band- In-Band (or inline) NAC solutions use dedicated appliances that it in between devices and the resources that they wish to access. They deny or limit network access to devices that do not pass the NAC authentication process. The "captive portal" NAC solutions found in hotels that hijack all web requests until the guest enters a room number are examples of in-band NAC. Out-of-band NAC solutions, such as 802.1X, leverage the existing network infrastructure and have network devices communicate with authentication servers and then reconfigure the network to grant or deny network acccess, as needed.
NAC solutions are often used simply to limit access to authorized users based on those users successfully authenticating, but they may also make network admission decisions based on other criteria. Some of the criteria used by NAC solutions are the following: Time of Day (Users may be authorized to access the network only during specific periods, such as during business hours), Role (Users may be assigned to particular network segments based on their role in the organization such as teachers being assigned to an administrative network to grant tem access to administrative systems, while assigning students to an academic network that does not allow such access), Location (Users may be granted or denied access to network resources based on their physical location, such as access to the datacenter network may be limited to systems physically present in the datacenter). Another criterion is System Health. NAC solutions may use agents running on devices to obtain configuration information from the device. Devices that fail to meet minimum security standards, such as having incorrectly configured host firewalls, outdated virus definitions, or missing security patches, may be either completely denied network access or placed on a special quarantine network where they are granted only the limited access required to update the system's security.
It is important to note that NAC (network access control) solutions are designed to manage the systems that connect directly to an
organization's wired or wireless network. They provide excellent protction against intruders who seek to gain access to the organization's
information resources by physically accessing a facility and connecting a device to the physical network. They don't provide protection
against intruders seeking to gain access over a network connection. For that, a firewall
is utilized.
Related Resources
